In today’s digitally-driven society, cyber security is critical. Every day, enterprises of all sizes face an onslaught of cyber threats. A proactive approach is required to properly negotiate this perilous terrain. The cyber security risk assessment is a critical tool for enterprises to use in identifying vulnerabilities, threats, and risks to their digital assets. This blog article will go into the subject of cyber security risk assessment, including its importance, major components, and methodologies for conducting an effective assessment.
The Significance of Cyber Security Risk Assessment
Digital Landscape Understanding
The cyber threat landscape is always changing. Risk assessments give businesses a detailed picture of the digital landscape, exposing potential vulnerabilities and threats.
Prioritizing Resources
Not all vulnerabilities are equally dangerous. A risk assessment enables companies to prioritize resources to handle the most critical threats, ensuring that resources are focused where they are most needed.
Compliance and Regulations
Many industries have specific cyber security compliance requirements. A risk assessment helps organizations meet these obligations by identifying gaps in their security posture.
Steps to Conduct an Effective Cyber Security Risk Assessment
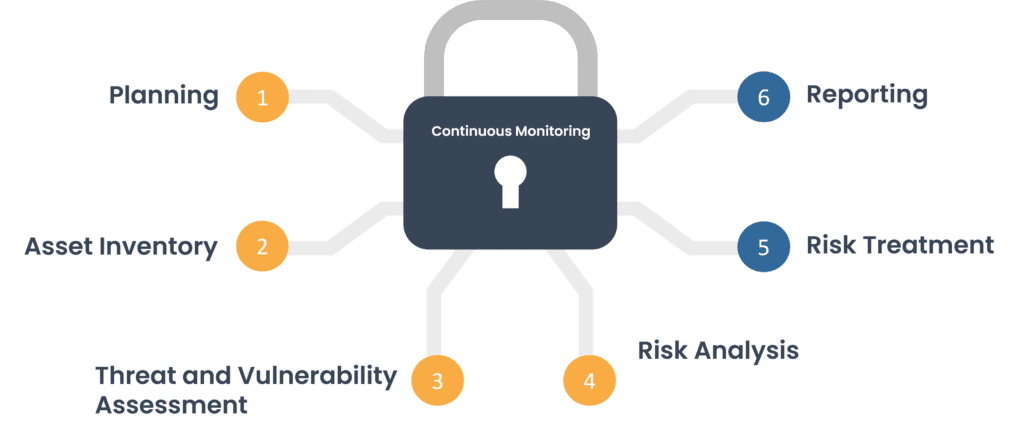
Planning
Define the scope, objectives, and accountable team for the assessment. Determine the methodologies and tools that will be used.
Asset Inventory
Make a thorough inventory of all digital assets, categorizing them according to their criticality and relevance to the organization.
Threat and Vulnerability Assessment
Potential threats and vulnerabilities can be identified using a variety of methods, including threat intelligence feeds and vulnerability scanning.
Risk Analysis
Consider the potential impact, likelihood, and any existing security controls for each highlighted risk.
Risk Treatment
Create a risk management plan outlining how each risk will be managed, including dates and responsibilities.
Reporting
Document the whole risk assessment process, including results and mitigation strategies. Create a report that informs stakeholders about the findings.
Continuous Monitoring
Cyber security is a continuous process. Review and update your risk assessment on a regular basis to account for changes in the threat landscape and technological environment.
Cyber Security Assessment Steps
Conclusion
An assessment of cyber security risk is not merely a compliance requirement; it is a strategic imperative. Organizations may preserve their digital assets and maintain customer and stakeholder trust by recognizing and addressing threats. Instead of waiting for the next cyber attack, conduct a thorough cyber security risk assessment and reinforce your digital fortress right away.











